Recently
I needed to pentest an Android application. When I installed the app to
my virtual device (Android Emulator), a pop up notification came out
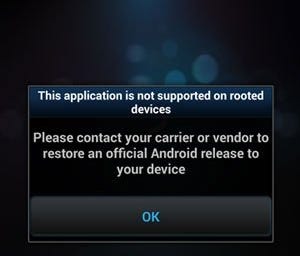
saying “This app can’t run in rooted devices”… so I needed a solution.
After a quick Google search, I found the first way… bypassing using an “Xposed” module.

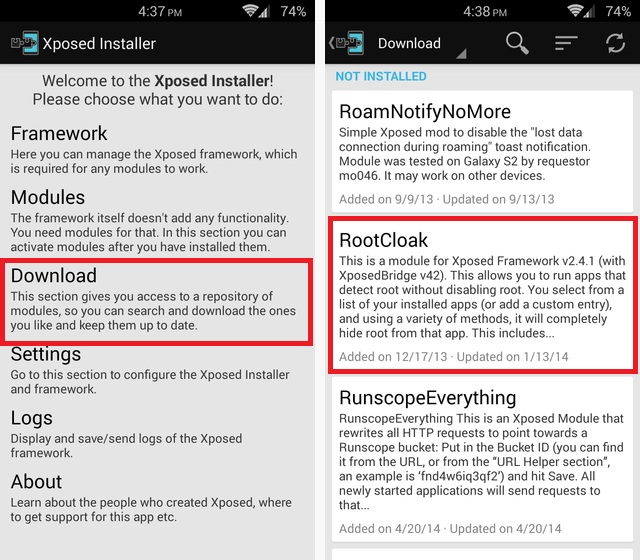
Bypass Root Check Using Xposed:1) Install Xposed
2) Install “RootCloak” (Xposed Module)
3) Open RootCloak > Add/Remove Apps > (select target app) and tap it.
4) Done! (open app and check if it’s works)
Unfortunately this didn’t work for me, so… let’s do this the “hard way” (or should i say… “old school”? :) ).
Bypass Root Check Manual Way:1) Decompile the APK file using “APKTool”
# apktool d /path/to/apk/target.apk -o /path/to/output/
(“d” for “decompile” and “-o” for output dir)
2) Most root detection techniques rely on checking for files on the OS that indicate the device has been rooted. Using GREP, search for any of the follow strings and change them to something random:
- Superuser
- Supersu
- /su
- /system/app/Superuser.apk
- /system/bin
- /system/bin/su
- /system/sd/xbin
- /system/xbin/su
- /system/xbin
- /data/local
- /data/local/bin
- /data/local/xbin
- /sbin
- /system/bin/failsafe
- /vendor/binNote: Other detection techniques look for any of the below-installed packages on the mobile device at runtime:
- supersu.apk
- Busybox
- Root Cloak
- Xpose framework
- Cydia
- Substrate3) Build the new version of APK with APKTool:
# apktool b /path/to/modified apk/target-new.apk -o /path/to/output/
(“b” for “build” and “-o” for output dir)4) Sign with jarsigner tool
# /path/to/my-key.keystore -storepass password -keypass password target-new.apk alias_name(You may need to generate the keystore first with keytool:)# keytool -genkey -v -keystore my-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity100005) Finally, install the new version and enjoy!
Bonus Track:If you need to bypass Certificate Pinning (in order to use the app with Burp Proxy for example) you can do this:
Bypass Certificate Pinning With “Xposed” module:
1) Once you have Xposed installed on your phone, search for “SSLUnpinning” module. Install it.
2) Open SSLUnpinning, look for the app on which you are trying to bypass the certificate pinning, and select it.
